Setting up Single Sign-On (SSO) - Okta
Note: Single Sign-On is only available on our Enterprise plans. Users with System permission can set up or manage Single Sing-On settings.
Cascade uses SAML 2.0 to securely authenticate and allow users to log in using Okta.
This guide is specific to Okta and assumes you already have an understanding of how our SSO solution works. If you're looking for a different SSO provider than Okta or want to read our main SSO guide, click here.
Assumptions
-
The setup guide assumes the user’s username in Cascade is the same as the email address in Okta. Please contact support if this is not the case.
Setup
-
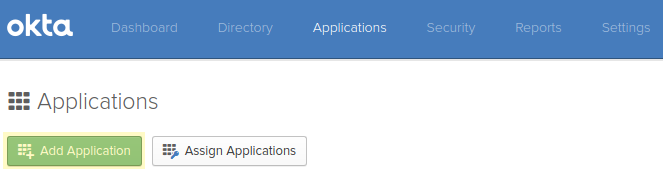
From the Okta admin dashboard, navigate to the "Applications" page and click on “Add Application” button
-
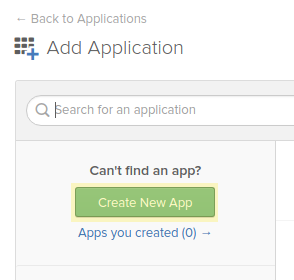
Click on “Create New App” button.
-
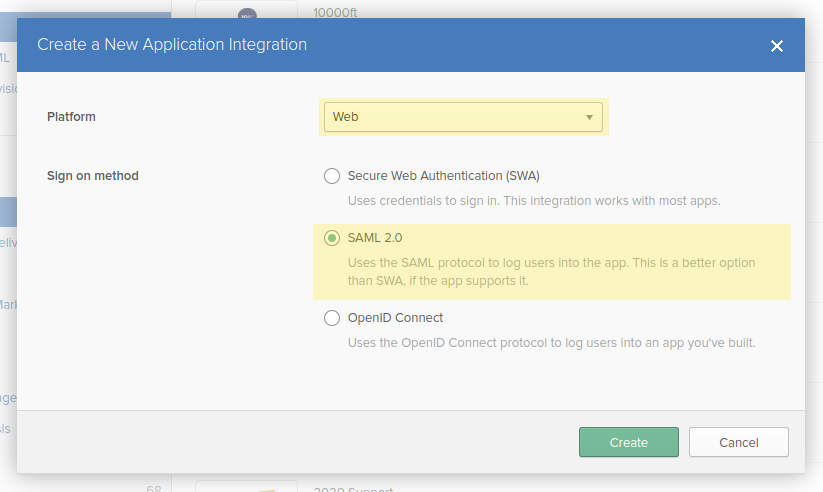
A dialog box should appear containing two input fields: Platform, and Sign-on method. Select "Web" for Platform and "SAML 2.0" for Sign-on method then click on the "Create" button.
-
Configure the "General Settings" section as you see fit then proceed to the SAML configuration section.
-
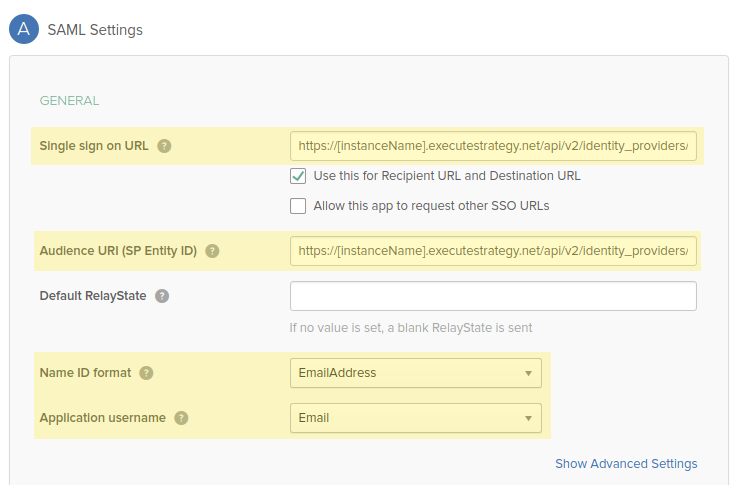
Configure the SAML settings as shown below, replacing "[instanceName]" with the actual name of your Cascade instance.
Single sign on URL: https://[instanceName].executestrategy.net/api/v2/identity_providers/1/login
Audience URI (SP Entity ID):
https://[instanceName].executestrategy.net/api/v2/identity_providers/1/metadata
-
Configure Name ID format & Application username according to what the users' usernames in Cascade have been set to. The configuration shown above assumes that the usernames are set to the users' email address. Note that username capitalization must match.
-
Click of the "Next" button to proceed to the "Feedback" section and configure the section as you see fit. Once the section is configured, click on the "Finish" button to finalise the creation of the application in Okta.
-
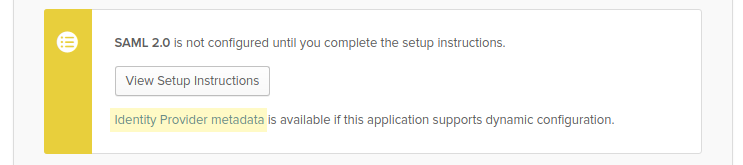
Follow this guide to register the Okta as an identity provider in Cascade using the values contained within Okta's generated metadata. The metadata can be retrieved from the application page within Okta as shown below.
You should now be able to access Cascade through Okta.
.png?width=200&height=80&name=Classic%20Experience%20(1).png)