Setting up Single Sign-On (SSO) - ADFS
Note: Single Sign-On is only available on our Enterprise plans. Users with System permission can set up or manage Single Sing-On settings.
Cascade uses SAML 2.0 to securely authenticate and allow users to log in using ADFS.
This guide is specific to ADFS and assumes you already have an understanding of how our SSO solution works. If you're looking for a different SSO provider than ADFS or want to read our main SSO guide, click here.
Requirements & Assumptions
-
Username in Cascade are the user’s UPNs in ADFS. Please contact support if this is not the case.
-
A server running Microsoft Server 2012 or 2008. This guide uses screenshots from Server 2012R2, but similar steps should be possible on other versions.
Setup
-
Create a Relying party trust
-
Click on “Add Relying Party Trust”
-
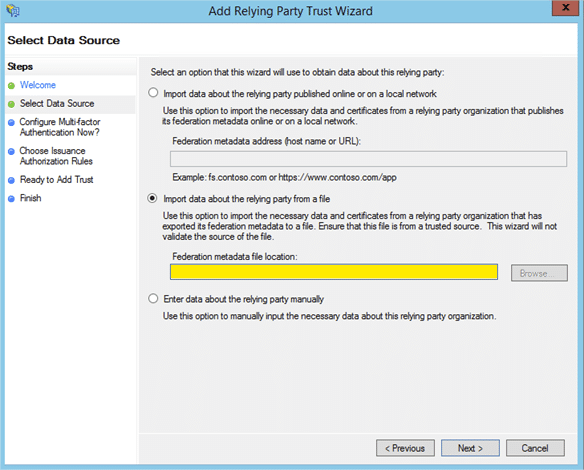
Follow this guide to register ADFS as an identity provider in Cascade using the values contained within ADFS's metadata. The metadata is usually located at https://[server]/FederationMetadata/2007-06/FederationMetadata.xml.
-
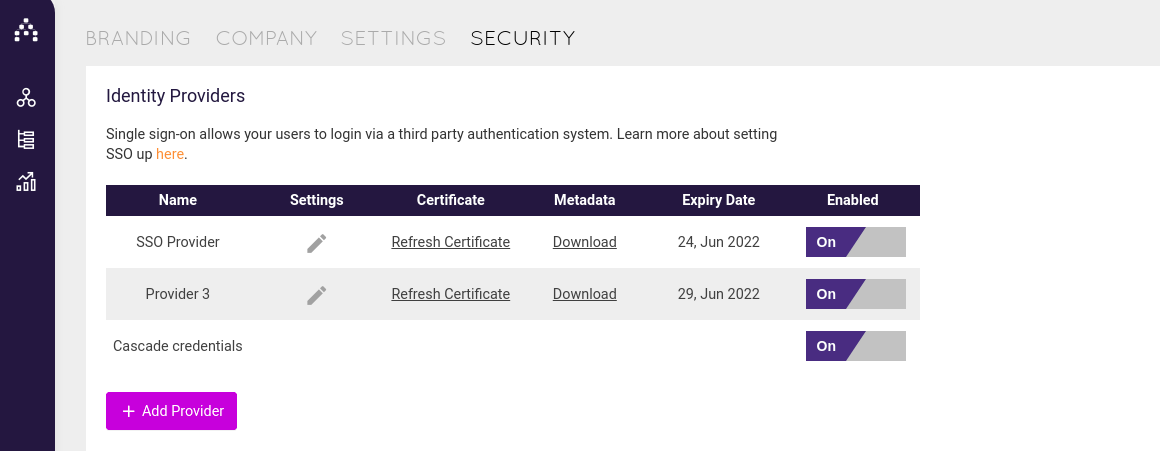
Once the IDP setup in the Cascade instance is complete, the XML metadata can be retrieved from: https://[instanceName].executestrategy.net/api/v2/identity_providers/1/metadata. You must be authenticate as an administrative user to retrieve the metadata. Alternatively, you can download the metadata from the Cascade Security web page by clicking the metadata "Download" button.
-
Download your Cascade instance’s metadata and upload it into highlighted field as shown above.
-
Continue through the Wizard until the Relying Party Trust has been added
-
Select the Cascade Relying Party Trust and click on “Edit Claim Rules…” on panel on the right hand side and click on “Add Rule…” on the “Issuance Transform Rules” Tab.
-
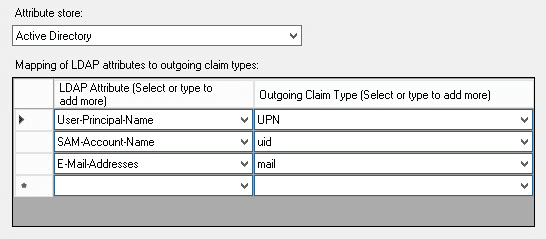
Select the “Send LDAP Attributes as Claims” rule template and populate it as follows:
-
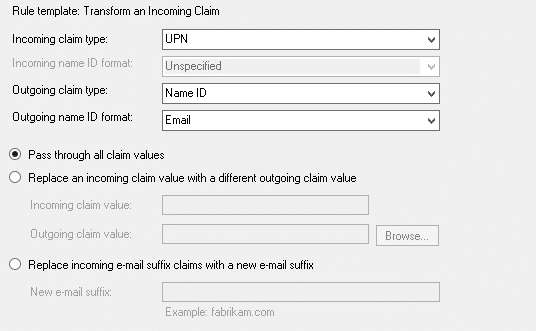
Add another Claim Rule but now select the “Transform an Incoming Claim” rule template.
-
Setup the rule as follows
You should now be able to access Cascade through the ADFS login page.
.png?width=200&height=80&name=Classic%20Experience%20(1).png)